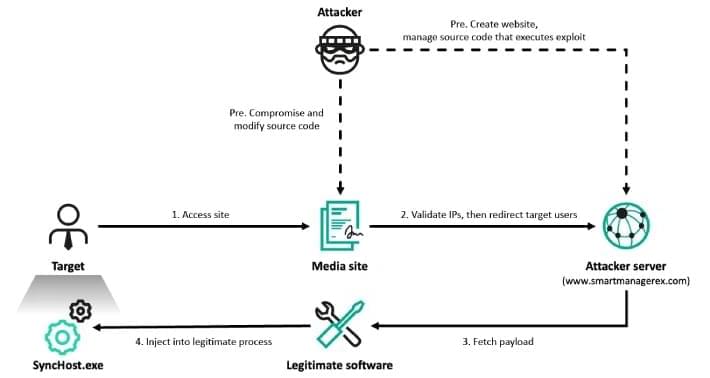
Cyberattacks can snare workflows, put vulnerable client information at risk, and cost corporations and governments millions of dollars. A botnet—a network infected by malware—can be particularly catastrophic. A new Georgia Tech tool automates the malware removal process, saving engineers hours of work and companies money.
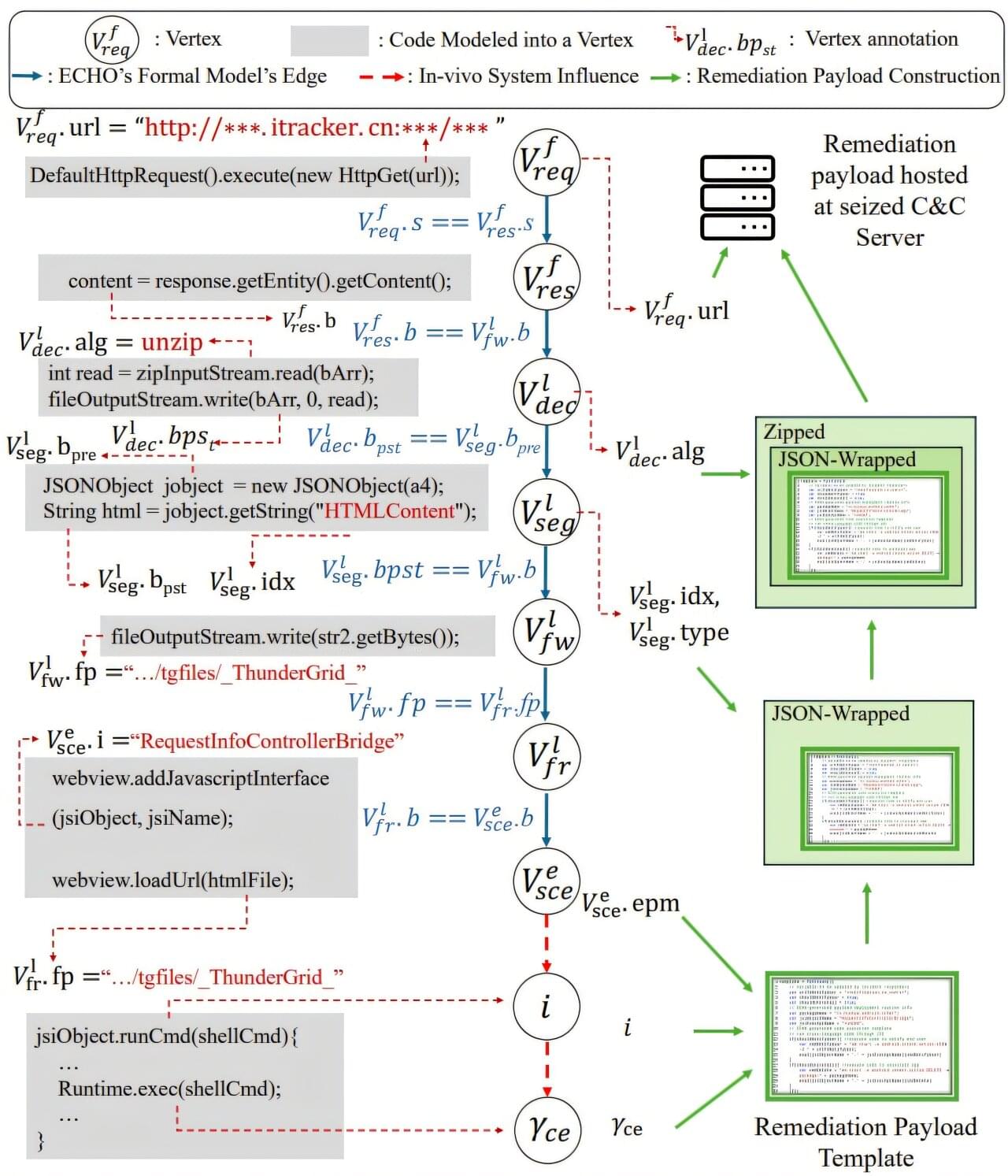
The tool, ECHO, turns malware against itself by exploiting its built-in update mechanisms and preventing botnets from rebuilding. ECHO is 75% effective at removing botnets. Removing malware used to take days or weeks to fix, but can now be resolved in a few minutes. Once a security team realizes their system is compromised, they can now deploy ECHO, which works fast enough to prevent the botnet from taking down an entire network.
“Understanding the behavior of the malware is usually very hard with little reward for the engineer, so we’ve made an automatic solution,” said Runze Zhang, a Ph.D. student in the School of Cybersecurity and Privacy (SCP) and the School of Electrical and Computer Engineering.