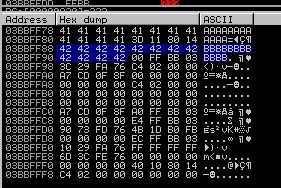
I want to write an exploit for a test application that provides only 12 bytes of space at the ESP. I'm not able to place shellcode in such a small space. I have no clue what I can do to solve this.
I have done the following steps.
- Fuzzing
- Find offset
- check for Bad chars
- find module JMP address
- control EIP
- use msfvenom for writing shellcode
I have tried to add 16 "B" but only 12 got written into the ESP space