
Some signed third-party bootloaders for the Unified Extensible Firmware Interface (UEFI) could allow attackers to execute unauthorized code in an early stage of the boot process, before the operating system loads.
Vendor-specific bootloaders used by Windows were found to be vulnerable while the status of almost a dozen others is currently unknown.
Threat actors could exploit the security issue to establish persistence on a target system that cannot be removed by reinstalling the operating system (OS).
Eclypsium security researchers Mickey Shkatov and Jesse Michael discovered vulnerabilities affecting UEFI bootloaders from third-party vendors that could be exploited to bypass the Secure Boot feature on Windows machines.
Secure Boot is part of the UEFI specification designed to ensure that only trusted code - signed with a specific, vendor-supplied certificate - is executed to start the OS booting process.
The firmware bootloader runs immediately after turning on the system to initialize the hardware and to boot the UEFI environment responsible for launching the Windows Boot Manager.
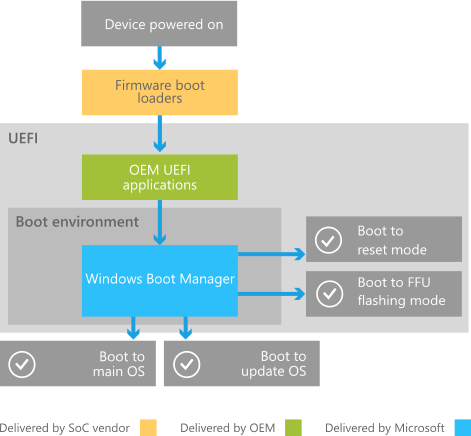
source: Microsoft
Eclypsium researchers found that three UEFI bootloaders that were approved by Microsoft had vulnerabilities that permitted bypassing the Secure Boot feature and executing unsigned code:
The three Microsoft-approved UEFI bootloads that were found to bypass the Windows Secure Boot feature and execute unsigned code are:
- New Horizon Datasys Inc: CVE-2022-34302 (bypass Secure Boot via custom installer)
- CryptoPro Secure Disk: CVE-2022-34303 (bypass Secure Boot via UEFI Shell execution)
- Eurosoft (UK) Ltd: CVE-2022-34301 (bypass Secure Boot via UEFI Shell execution)
Microsoft has worked with the last two vendors in the list above and released security update KB5012170 to fix the problem in the provided bootloader.
As part of this fix, Microsoft has blocked all of their required certificates that were issued with the Security Update Release from July 2022.
"This security update addresses the vulnerability by adding the signatures of the known vulnerable UEFI modules to the DBX" - Microsoft
Eclypsium notes that with bootloaders from Eurosoft and CryptoPro Secure Disk an attacker could evade Secure Boot by leveraging the signed UEFI shells (esdiags.efi and Shell_Full.efi) to read and write to memory, list handles, and map memory.
The researchers say that exploiting the vulnerabilities in these two bootloaders "could be easily automated using startup scripts."
Since the behavior of these two shells is visible on systems with a monitor, users may might notice a red flag.
However, exploiting the vulnerability affecting the New Horizon Datasys bootloader is much stealthier and users would not have any indication of an attack.
"This bootloader contains a built-in bypass for Secure Boot that leaves Secure Boot on but disables the Secure Boot checks" - Eclypsium
Threat actors exploiting CVE-2022-34302 would have an easier task on their hands than with the other two flaws and could disable security handlers by executing unsigned code directly.
Eclypsium researchers say that exploiting CVE-2022-34302 is so easy that adversaries are "highly likely" to try to leverage it in attacks.
Attackers exploiting any of the three vulnerabilities require elevated permissions on the system, such as admin on Windows or root on Linux machines, which is far from difficult to achieve on both platforms.
In an advisory this week about the vulnerabilities, the Carnegie Mellon CERT Coordination Center warns that code executed in the early boot stages could “also evade common OS-based and EDR security defenses.”
Carnegie Mellon CERT CC has provided a list with 23 UEFI bootloader vendors, a clear status being available for just three of them: Microsoft (impacted), Phoenix Technologies (not impacted), and Red Hat (not impacted).
The rest of the 20 vendors have also been informed about the issues but it is currently unknown if their products are affected or not.
The list includes names like Acer, AMD, American Megatrends, ASUSTeK, DELL, Google, Hewlett Packard Enterprise, HP, Lenovo, Toshiba, and VAIO Corporation.
A fix for these vulnerabilities should be delivered either by the Original Equipment Manufacturer (OEM) or the OS vendor by updating the UEFI Revocation List - the Secure Boot Forbidden Signature Database (DBX), a database of revoked signatures for previously approved firmware and software that starts systems with UEFI Secure Boot.
Before applying the update the DBX revocation list only after first making sure that the device is not using a vulnerable bootloader or after applying the bootloader update from the vendor, if available.
Update [Monday, August 15]: Added information from Eclypsium that appeared after publishing this article.







Comments
nqu35e - 2 years ago
it only work for Organisations and companies but not for individual users of window pc, it is impossible to block because the individual had their pc is being controlled remotely by unknown online Admin, the UEFI had already been switch off and the the window they are using is booted from a partition in the hard drive set as default and that window is in the container. Unless microsoft block or remove "Default Migration setting" , this Malware settings does not come from outside, it came from within old window files being migrated to the new pc, the moment you start seeing Microsoft account problems, privilege escalation is taking place and you will not be default user anymore in your pc, it as been overtaken. this is what is going on currently and microsoft is very far away from the reality on the ground, one you get infected, you will be in the malware memory for default migration settings, the UEFI will be switch off does not matter what security microsoft put there, it is real, does not matter if you install new window, it is damage for life.
BH0 - 2 years ago
Watch as thousands of PCs around the world wont boot :D Im not convinced that Microsoft is to blame, I think the process can be attacked by design. Certainly, no system will be ever 100% bulletproof. In the sake of increasing security from 99,97% to 99,98% on 10 000 devices, we will break another 1 000 000 fully functional systems. UEFI Secure Boot is turned of on nearly 50% of devices. Some dont even have UEFI, but rely on good ol' BIOS.
We are civilisation of safetiness. Civilisation of overly sensitive beings. Shame on us :D
Time to redesign UEFI to BNB (brand new boot - for example).
nqu35e - 2 years ago
Yes, new boot system soldered on the motherboard separately, non programmable and nothing
can be added to it.